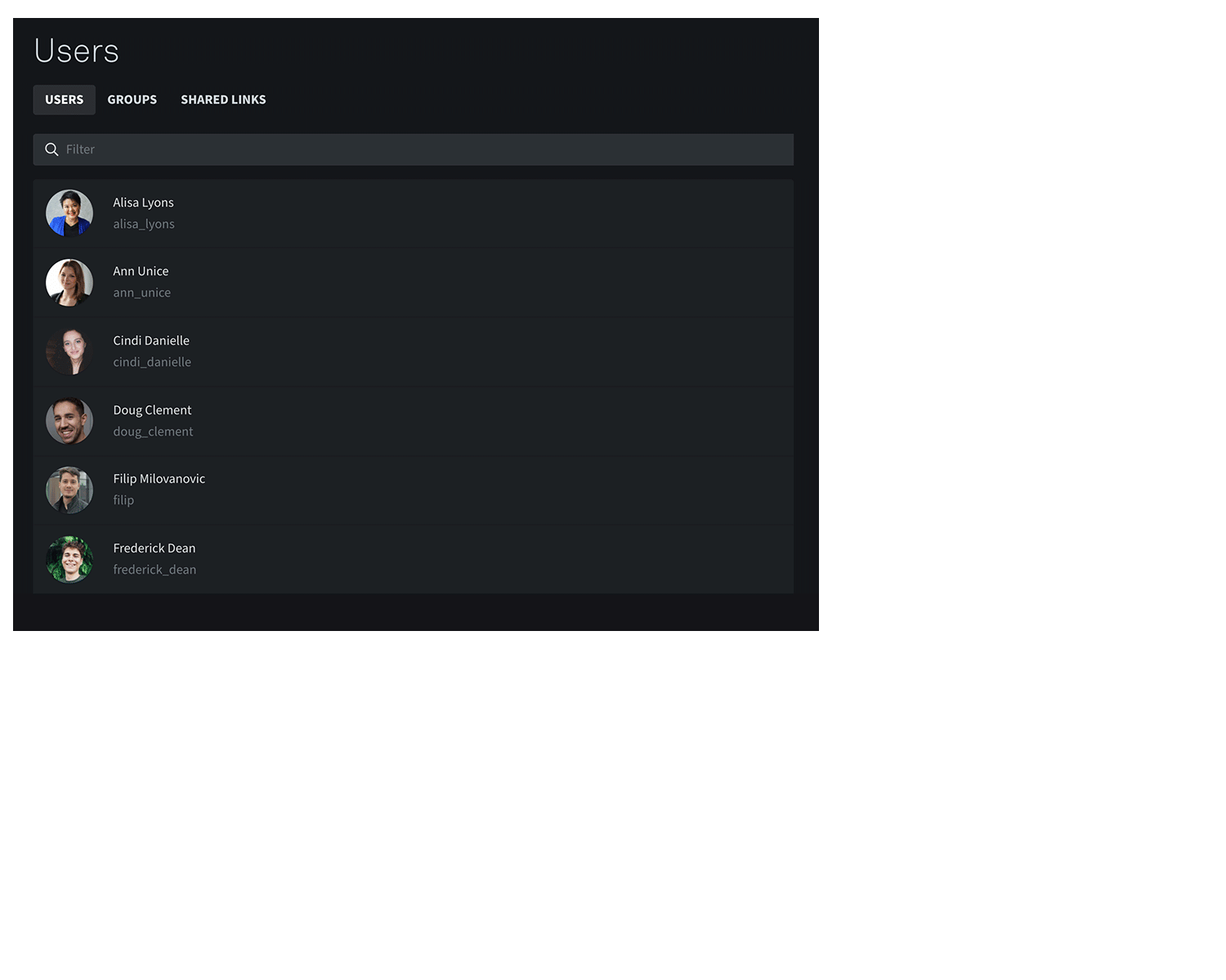
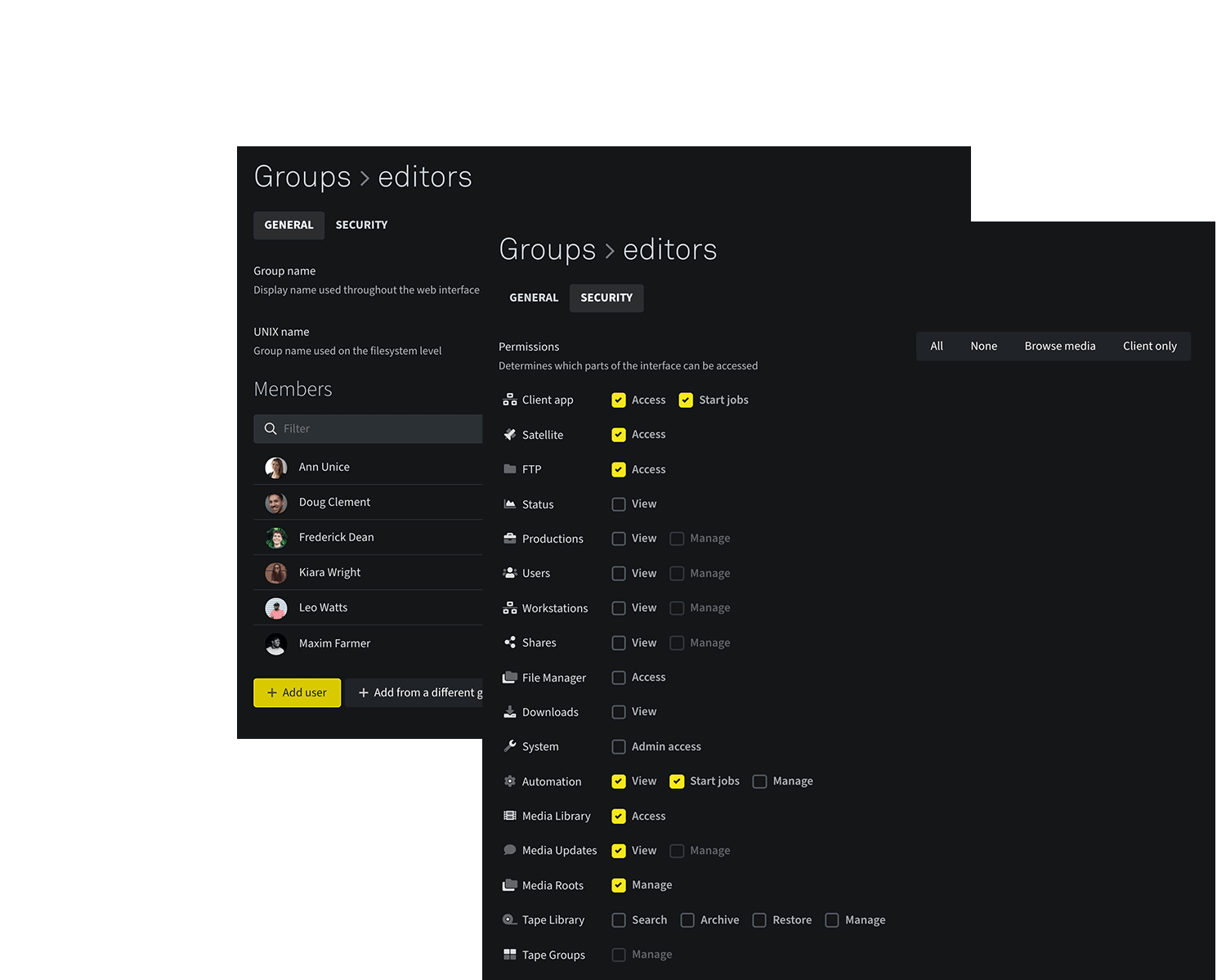
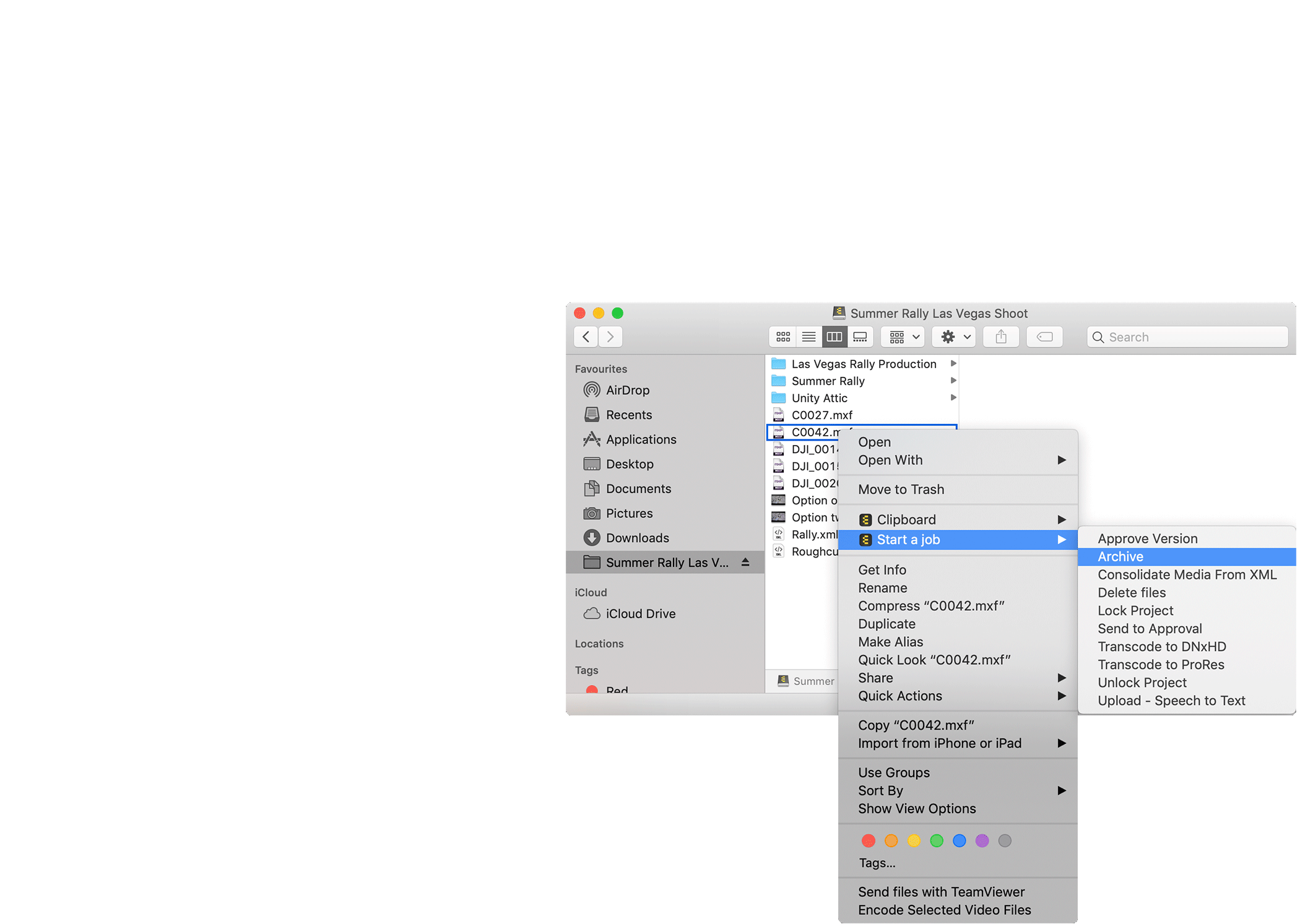
Geared for security and easy to use
Your environment may require limiting access to the internet through a DMZ-node or „safe listing“ specific URLs through the internal network (LAN). The ELEMENTS system supports these requirements and provides optimum encryption for enhanced security. ELEMENTS systems accomplish this by enforcing TLS 1.2 protocol or higher and utilizing a limited set of trusted cryptographic ciphers with maximum complexity key strengths / DH Parameters and HTTP header configuration. Furthermore, if needed, ELEMENTS systems support complete data at rest and data in transit encryption.